The phases
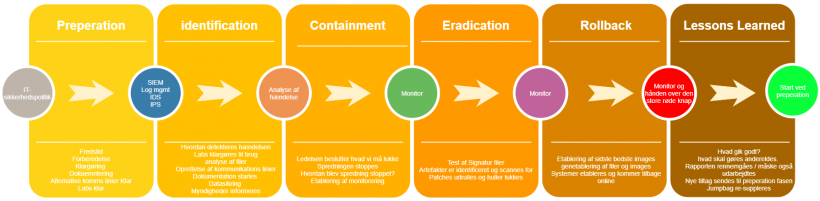
The phases are the periods you as a company have to go through to handle an attack. Here you get the outline of the phases based on my own experience (and the textbook's). You can access a more detailed area if you are in the class
Preparation
Peace time where you prepare all the activities and tools (both software and hardware) before something goes wrong. here you will also have control of all the documents to be used during an attack. These are the plans, processes and procedure that come out of an Incident.
Here we talk about the link to governance, IT security policy, IT contingency plan, IT crash plans and IT attack management
Identification and analysis phase (Identification)
This phase is when something goes wrong. It escalates to the type of incident, whether it is safety related or common crashes.
When the plan is activated, it is based on an assessment that it is security related.
It must start with data collection and identification of what has happened and how it has come in. The behavior of the malicious files must be analyzed. What they do of new malicious actions and what domains IP addresses they contact.
Lockdown (Containment)
When we have become wiser about how we are affected and what has happened. Then we can start looking at how we utilize our knowledge to block the attack. Of course, this requires that we have some tools / technologies to assist us with the shutdown.
A few examples.
If we know domains and IP addresses, they can be blocked in eg DNS, Firewall, Proxy etc. If we know files that are created, then they can be blocked in the antimalware solution on end points, servers, IPS etc. If we know the HASH of the files, then they can be detected by a scan. If we know the characteristics, then we can create YARA rules, which give an alarm when we see patterns. (alarm only) If we know the spread, we can, for example, close shared drives
These are some of the examples of detection and blocking. It can vary from incident to incident.
If you find out that something was missing to analyze, or new data has been added. This does not prevent you from going back and doing a new analysis of the malware or artifact.
Recovery (Rollback / Restore)
Once we have stopped the attack, it is important for us to be able to find out when "day zero" was. That is, the separate date where we can identify when the incident took place and we can recreate from before this date / time
Monitor phase
If you have an attack that has been more extensive, you can implement a monitor phase.
It can be a few days up to weeks and months where you intensify your monitoring. If something happens, you can press the "big red button" and lock your environment down again, so you inhibit a possible re-infection.
Back to normal (Post incident / Lessons Learned)
Here we start normal operation and end the process / phases themselves.
We gather for a meeting where you turn what went well or badly. Get the air cleaned if it got a little hectic. What we learned is collected and from there a report is prepared as a summary of what we learned and how it is introduced in the plans we have.
So we have an updated "Business Continual Plan" which gives the company "Continual Service Improvement"
Flow in the phases
It is an excerpt for the NIST way (with 4 phases)
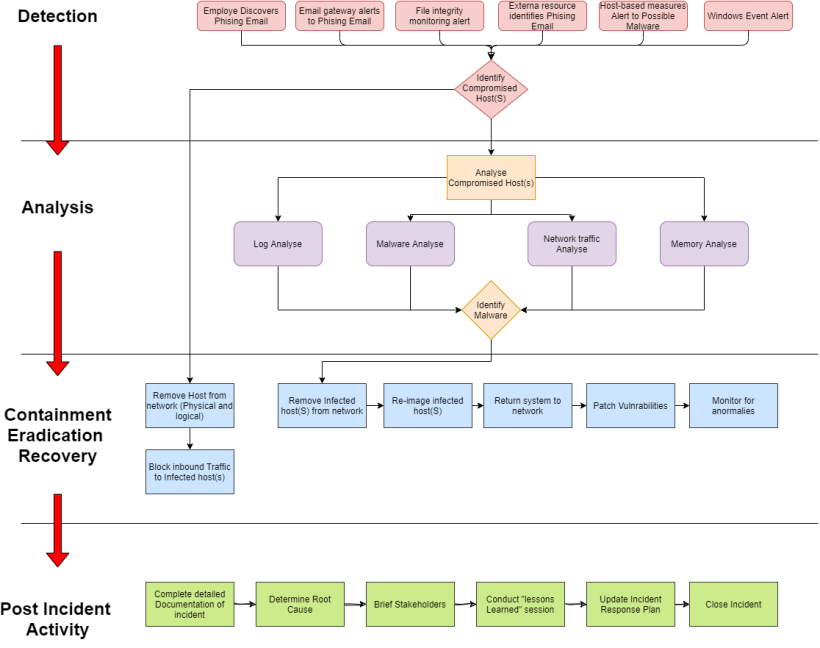
- NIST 4 phases *
SANS version
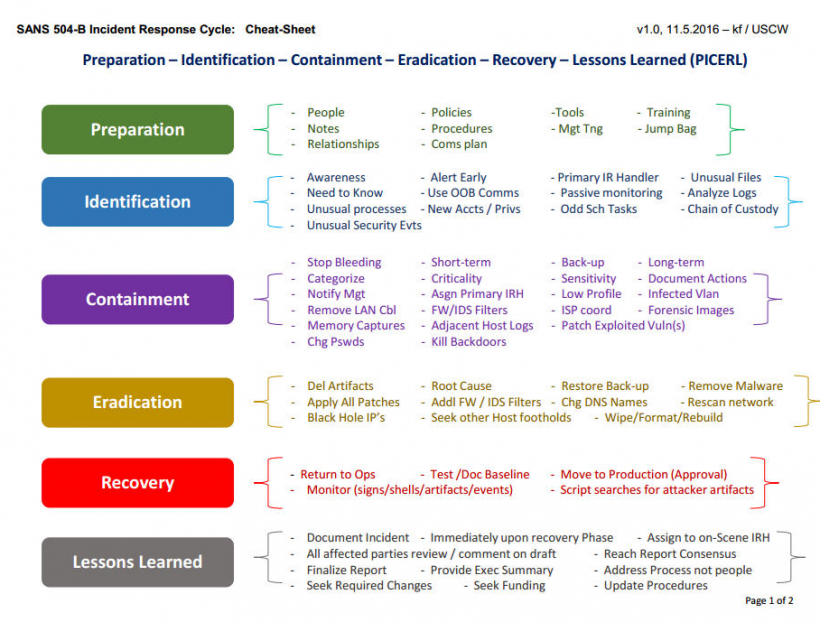
Can be downloaded from [SANS website] (https://www.sans.org/media/score/504-incident-response-cycle.pdf)
