Memory forensics case
How do you put this in to use ? Well there are many different scenarios that can come into play here. In my example i want to pull out a users password from the memorydump.
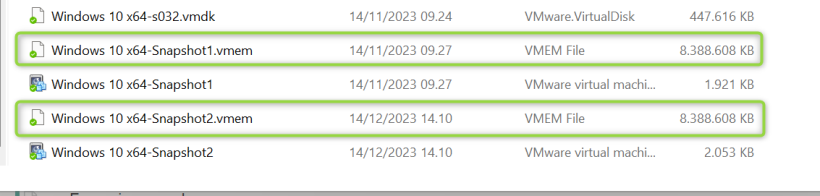
I have secured the memory dump with FTK imager. You can also use VMware, by suspending the virtual machine and then pull out the .VMEM file
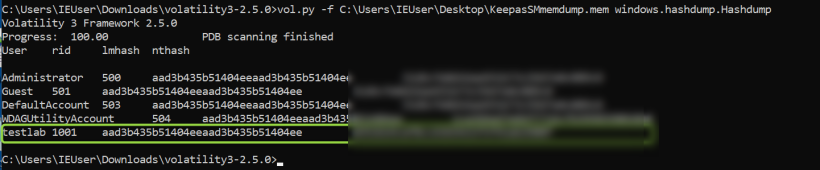
Then load volatility and run the command
vol.py -f C:\Users\IEUser\Desktop\KeepasSMmemdump.mem windows.hashdump.Hashdump
Output was = 43239E3A0AF748020D5B426A4977D7E5
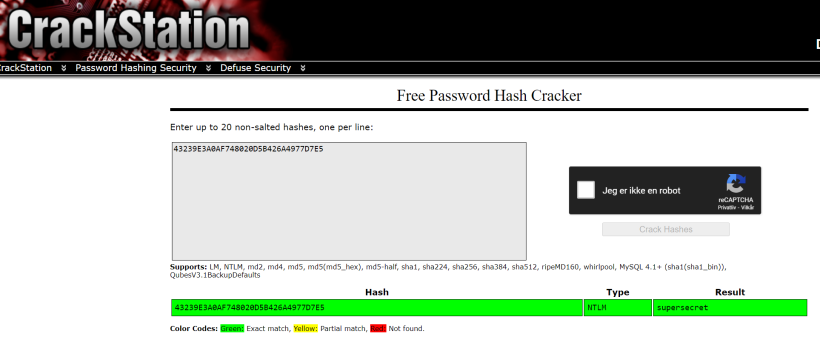
There you have the password for this machine.
